
Cyber Exposure Platform
Designed for Law Enforcement and Security Service Providers, the CIH platform enables cyber security professionals and investigators to discover and explore Dark and Deepweb activity in a productive and efficient way.
The platform provides users a single point of access to a vast archive of evidence from restricted sources such as Dark Web Markets, Leak Platforms, and Discussion Forums that keep on growing in real time and dating back multiple years.
EXPOSED INFORMATION
EXPOSED SYSTEMS
CONTINUOUS TESTING
Automation is unique to Cyber Intelligence House. Start vulnerability scans with one click and zero configuration based on the assets that you have discovered.

Investigations

Benchmarking
Compare cyber exposure and results to a peer group based on location, industry or size.
Understand and visualize trends from the same peer groups to create industry or region specific analysis.
EXPOSED INFORMATION
EXPOSED SYSTEMS
CONTINUOUS TESTING
Automation is unique to Cyber Intelligence House. Start vulnerability scans with one click and zero configuration based on the assets that you have discovered.

Investigations
Investigation module allows investigators and law enforcement to conduct investigations, searching and monitoring actors, events, transactions and other content in the dark web and deepweb.

Benchmarking
Compare cyber exposure and results to a peer group based on location, industry or size.
Understand and visualize trends from the same peer groups to create industry or region specific analysis.
With CIH platform, the users will be able to search, detect, analyse, respond to, report on, and prevent cybersecurity incidents that were previously impossible to find.
ACCESS RAW DATA
PROJECT WORKFLOW
LEAD SCANNER
Lead scanner allows you to assess up to 300 organizations at once. Pre-screen or conduct due diligence of potential customers.

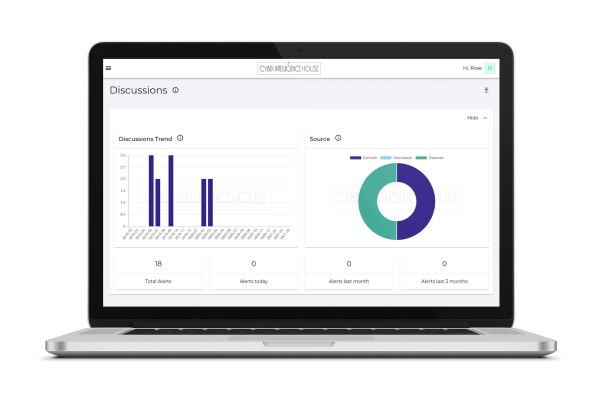
Analysis & Graphs

Reports & Export data
What you see is what you get.
You can export any findings in different formats such as CSV, PDF and PPT to mention a few.
ACCESS RAW DATA
PROJECT WORKFLOW
LEAD SCANNER
Lead scanner allows you to assess up to 300 organizations at once. Pre-screen or conduct due diligence of potential customers.

Analysis & Graphs
Our user friendly user interface provides time series, trends, distribution and other types of graphs that you can embed in your reports.

Reports & Export data
What you see is what you get.
You can export any findings in different formats such as CSV, PDF and PPT to mention a few.
Balances both machine learning AND human analysts
Connects threat information directly to business operations
Provides threat mitigation recommendations
Creates a tailored risk profile
An immediate intelligence operations and results without additional staff
Provides view on key metrics such as Mean-time-to-identify and mean- time-to-repair
Continuous penetration testing & red- teaming
Validates threats against a standardized information model
Uses non-technical language to explain cyber risk
Runs the data acquisition, doesn’t rely on open source feeds
Alerts you only about relevant threats
Integrates with existing cybersecurity environment
Continuous infrastructure testing with zero configuration
Key person risk monitoring
Delivers only intelligence on customer-specific threats
Helps identify how best to direct cyber-related resources
Provides insight into active threats via the Dark Web, Deepweb, data breaches
Provides specific mitigation recommendations
Integration – API that connects to EDR, SIEM, and SOAR
Continuous application level testing


