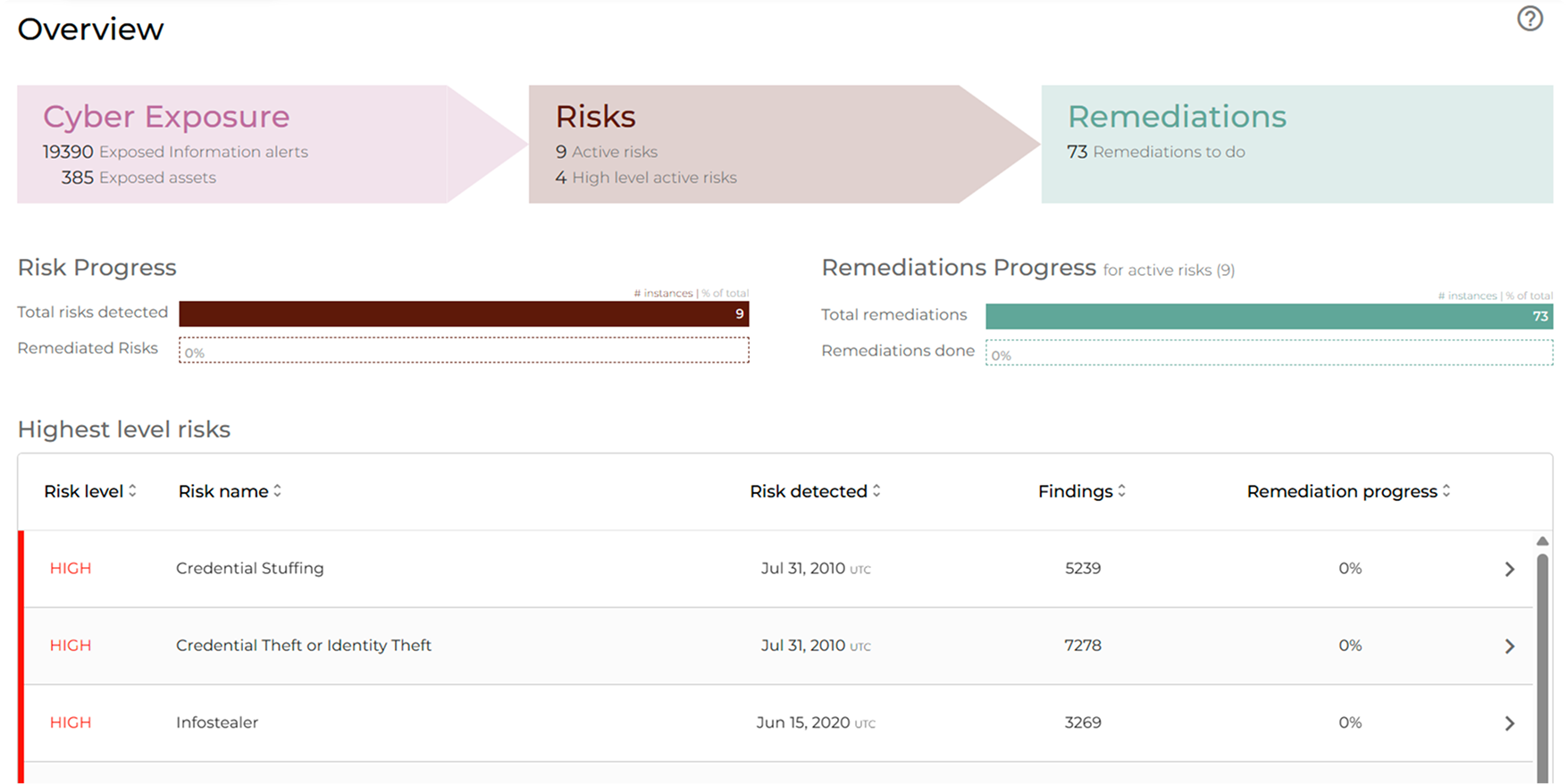
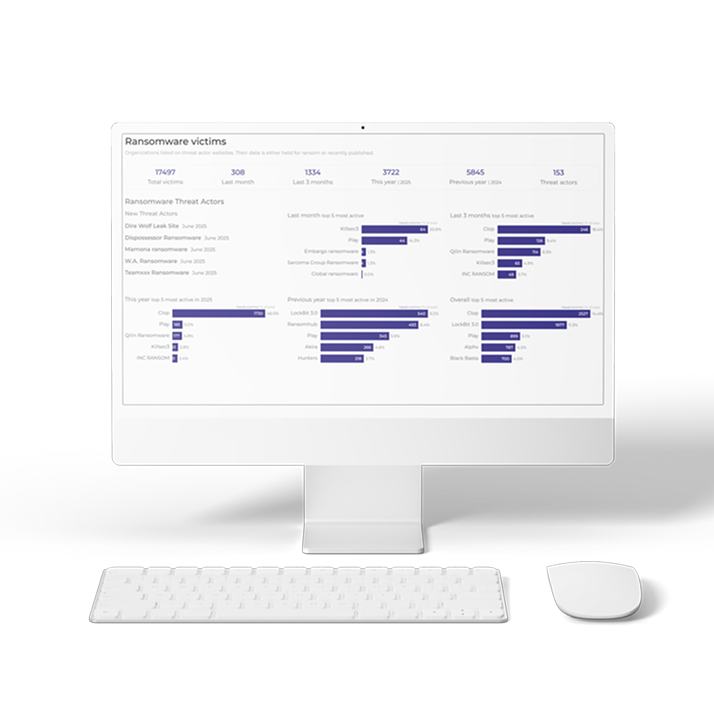
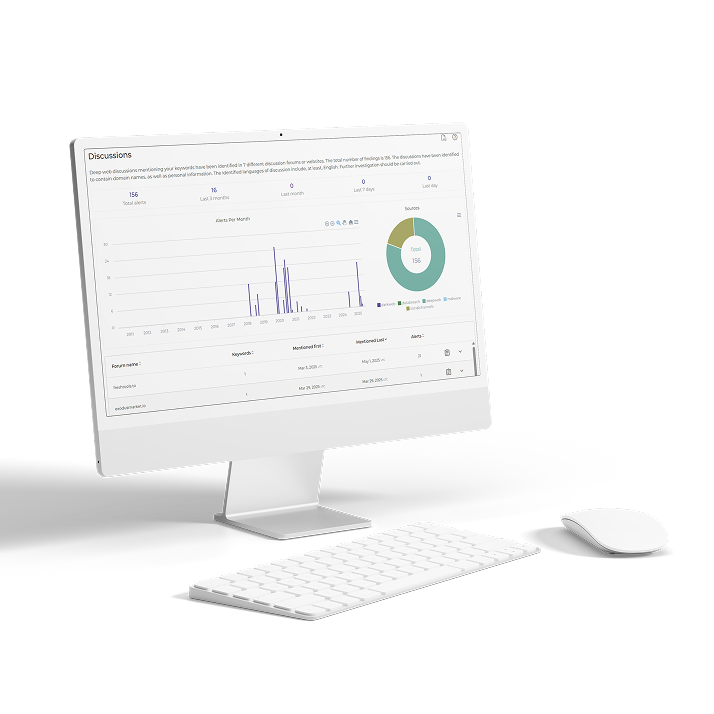
Cyber Exposure Platform
Find out how the Cyber Intelligence House platform can provide unmatched data from the dark web, deep web, breaches, and malware logs

Resources
Our resource library is
packed full of useful information, from videos to whitepapers you can find it
all here.