Risk management is a practice, a profession, and a bit of a science. It also has measurable, real-life effects.
What Is Risk?
The basic formula of risk says that it is the probability that something unwanted will happen multiplied by its total impacts. In a personal context, it means if I cross the street, there’s a likelihood that somebody is going to hit me with a car unless I’m careful. So I’m making a personal risk-management decision by looking both directions before I step off the curb.
In cybersecurity, risk is often approached from a technical angle. We can measure risk by assessing exposure, vulnerabilities, likelihoods, exploitability, impacts, and so on. For example, how many people do we employ that could be fooled by phishing attacks? Or how many systems do we have online that could be hacked? Using that information, we can then do technical measurements to deduce how high our total IT or cyber risk is.
Risk = Probability × Loss
Risk management strives to give quantitative value to risk, but it often requires significant qualitative analysis as well. Even if the risks are assigned numerical values, each one is subject to the opinions of a variety of people from different departments. Each will likely give a different answer.
If the risk managers try to use one single method to assess all types of risks, the formula won’t be applicable to all situations and won’t create meaningful results for the company. In fact, a professor we know did a review of different risk analysis methods to find out how many different types he could identify. He found more than 100 different formulas for calculating risk. So in practice, a cybersecurity manager must deal with an indefinite variety of risks and dozens of possible ways to analyse them. Remember, risk management is not just quantitative but qualitative too. The cybersecurity manager must always consider additional ways to describe the situation because reducing the problem to a single number filters out important information.
Assess Risks Regularly
Risk management is most effective when it’s done frequently and continually, with the lightest possible footprint, then updated and revised on an ongoing basis. Too many companies do risk analysis once a year, update it for the following year, then forget about it until the next year comes around. That doesn’t work.
Some periodical reviews of risks are necessary, though. We’ve found that it’s quite effective to meet quarterly with the key people responsible for operations, leadership, and management. In these quarterly meetings, the participants should spend fifteen minutes to half an hour talking about the most obvious, major risks, then write down the results of that conversation. Regular communication keeps the cybersecurity manager in the loop—management is often aware of existing and emerging risks that might not be obvious to the cybersecurity manager.
On the other hand, leadership won’t know about all the risks in every department. If the cybersecurity manager is working with a company with no other risk management people on board, it’s his or her job to ask the different departments to do their own risk analysis work periodically and then report their findings to the cybersecurity manager. (If the company already has other risk management people, the cybersecurity manager would be wise to use their services instead of trying to run the whole show alone.) When all known risks are pulled together, and the largest risks are communicated up the command chain, this is called risk consolidation. Smaller risks are left down to be handled at the lower branches of the organisation, and bigger ones are communicated upward. The cybersecurity manager should understand this process and know how it works.
Risk Management Process
Risk management is a process, and we usually start by identifying and assessing risks. In a smaller company, cybersecurity manager might arrange a workshop all by himself. In that workshop, people come together to identify potential risks. The workshop should start with identification, then proceed to discussing how likely and harmful the risks are.
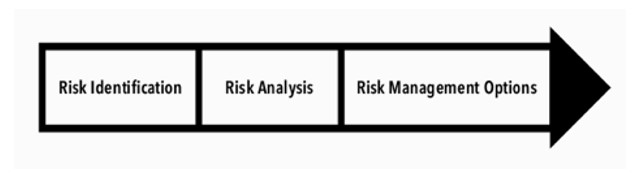
After that, we decide what to do about each risk—mitigate it, avoid it, share it, or even accept it—we call these risk management options. Mitigation means making risks smaller, for example, by implementing an additional security technology or a process so that the risk becomes either less likely or its impacts are alleviated, but the risk may not go away entirely. Avoidance means rejecting the risk altogether by pursuing that avenue. If we know a country is at war, we choose not to travel there. That’s risk avoidance. Risk can also be shared between parties, for example, the company and insurance company—for a price. Or senior management may want to simply accept a risk and sign for it. This is also an option!
Most Common Risk Management Options
- Avoidance (stop doing the risky thing in business)
- Mitigation, or reduction (optimise – mitigate)
- Sharing (transfer, outsource or insure)
- Acceptance or retention (decide to keep it)
Subscribe To Our Newsletter
Get the latest intelligence and trends in the cyber security industry.
Unidentified Risks
One of the biggest security threats to security is management that doesn’t even realise there is a risk. Or, if they do recognise a risk, they don’t take ownership and assume someone else will handle it. For example, in a factory, the production manager may not feel that business interruption risk is their problem if data connectivity goes down. He believes that’s an IT problem, so he doesn’t bother to build redundancy. When the data connection line goes down, he blames IT. He may avoid blame, but he doesn’t avoid the threat itself; the production line still goes down.
Many managers, even if they recognise the risk and agree who owns it, may not comprehend the magnitude or possible impact of the risk. Too often, risk is underestimated. For example, it may be fairly simple to estimate the probability of a communications’ blackout, since it might happen once or twice a year, maybe three times. If it happens that often, it’s quite probable it will happen again.
What is the impact of these blackouts? By collecting the data on the previous incidents, a cybersecurity manager can answer many questions about impact: How much did it cost to fix? How much damage was caused? Was it direct or indirect damage? Answering those questions provides a clear picture of how much it could cost in internal labour, incident management, external costs, and so on. The nice thing is that when you can quantify a risk, you can ask for a budget to address it.
Quantifiable vs. Qualitative Approaches
Risks like damage to reputation or hindering future growth are hard to quantify, and yet these subjects are top concerns of business owners. Successful risk managers or cybersecurity managers have to address both. If they cannot put a figure on it, they’ll have to sell their plan another way, like telling the story of how things are likely to turn out if the risk is not properly addressed and then defending the estimation of how serious the risk is.
For new business ventures, like a startup that’s launching a new product line, it can be useful to ask them to identify scenarios that could be catastrophic to the business. Help them think about what could be bad enough to bring the company to a standstill. Scenario analysis like this will drive your point home. The simplest kind of scenario analysis is when people come together in a workshop and come up with causes and impacts in a catastrophic business risk scenario. Let’s say they are setting a joint venture with a business partner. In the workshop, they could identify indicators for failure of that venture. If these indicators should appear later, it might mean that the scenario is materialising. This is very close to business management, and a purely qualitative approach to managing risks.
How About Quantifiable Risks?
The ultimate goal of risk management is to quantify risk and make it relatable to the business. Risk management is about minimising the downside of business decisions on all levels of the corporation. That allows the company to take more risks and to take advantage of more opportunities.
Risk managers ask questions like, “Can you tell me how often this potential risk turns into an actual problem? What’s the probability? What’s the impact in terms of money, life, property, downtime, or business interruption?” They will be interested in qualitative and quantitative data.
Risk management people will first identify risks, then try to understand them, assessing each risk either quantitatively (in terms of money) or qualitatively, if the numbers are vague. They will put the risks in order of priority with the bigger ones at the top. The cybersecurity manager should meet risk management people and make them explain how risk management works in the company, including where to report risks, how they are assessed, and how to participate in the process.
Example of a Quantified Risk
For example, if the business has been experiencing network outages, this is clearly a risk that needs to be assessed and explained. Five outages per year, causing $100,000 loss each, means a $500,000 per year cost. Investment-wise, it would make perfect sense to put money into network resiliency and enjoy a good return on the investment going forward.
Quantification Homework
Let’s say you are an investor and you expect to get a 10 percent return on investment. How much would you be willing to pay to make $500,000 by reducing operational losses due to downtime like in the example above?
Put the Risks into Right Buckets
When the cybersecurity manager is faced with prioritising risks, it can be helpful to group risks by category. There are many ways to categorise risks. We’re using one traditional four-category system here, but you might want to look up other frameworks as well, like COSO ERM.
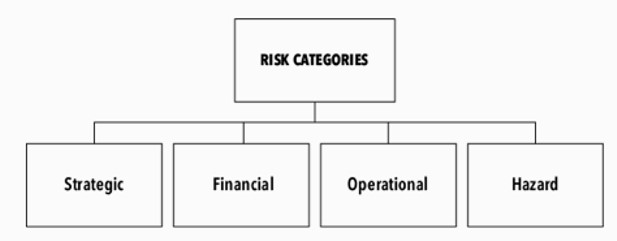
The first category, and the most obvious one, is hazard risk. That means things like a fire, flood, tornado, or heavy rain. These risks are usually well managed and covered by regulations. For example, automatic fire extinguisher systems are required in office buildings. There’s a lot of hazard risks to control when setting up a server room!
The second category is operational risk. This category includes things that companies do to limit their exposure to operational risks, like communications’ breakdowns or IT system breaches. Locks on the door are for operational risks of burglary in the office. You’re not really required to lock the doors by law, but you still do. Many of our commonplace cybersecurity risks and related technologies fall under this category.
The third category is financial risk. There are many different types of financial risks, including theft, counterparty risk, foreign exchange risk, market risk, cost of capital risk, and so on.
The fourth category is strategic risk, which encompasses larger issues, like growth strategy risk, branding or image risk, competition risk, customer and industry strength, change risk, and the risk of becoming obsolete. One example of strategic risk is a technology risk. When it materialises, the company’s products may become obsolete in a short time because of leaps in competing products. Nokia was a victim of technology risk. In a few years’ time, they disappeared off the map.
Risk Registers and Governance
One of the tools used in risk management are risk registers. It might be called something else, for example it might be part of a GRC framework (Governance, Risk and Compliance). GRC is usually managed with a specialised software, but the concept of risk register is the same: it’s covering a list of risks among other things. A team of analysts maintains the risk register, maybe within an application or an Excel spreadsheet.
The concept of a risk register is sound, but if the risk management function isn’t focused on one specific type of risk, the team will collect a wide range of different types of risks in that register, and it will become unwieldy. Risk management for the sake of itself isn’t very useful. For instance, say one department has an antivirus problem, a different department has a financial fraud problem, someone else has a health hazard, while a VP is talking about business venture risk and strategy initiatives. All of these risks, each with different impacts and probabilities, will end up in the same risk register. The register will then become bloated. It turns into the final resting place of a collection of bad things in the company that nobody is doing anything about, rather than a call to action. One case we have seen involved a financial institution that used their risk register to collect everything in one place. The register had fifty columns to be filled out for each risk. These people missed the point of why risk registers exist. They exist so that risks can be compared and communicated effectively, not because risks can be managed through the tool. A risk register is not a management tool. In fact, it’s very difficult to even manage a list of that size; it would require a full-time position just to maintain that spreadsheet.
It’s important that the register doesn’t become a dumpster for all risk items because it’s too easy for management to forget items once they’re relegated to the register. The risk register shouldn’t become a bloated monster. If it’s too big, there’s no way to bring it to the table for people to talk about it. In reality, there’s always more risk than you can actually handle, but if there are too many risks on the register, they can’t be prioritised effectively. Instead, select only the top handful that you want to act on and focus on those.
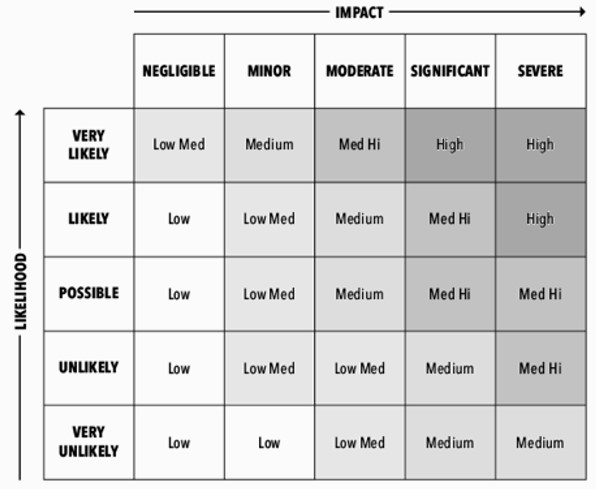
Visualise with a Risk Matrix
People in risk management often use a risk matrix to estimate and rank each risk in relation to other risks and then prioritise accordingly. This allows them to visualise different risks and present them more understandably to senior management. A risk matrix can give a hint to which risks should be handled first. There is a pitfall though; a five-step risk rating system like the one below looks good on paper. But how skillful are people really in assessing the likelihoods of different risks? How about their impacts? Give the same risk analysis task to several people independently, and you are sure to get different answers.
Risk Prioritisation and Planning
If there are twenty risks listed, the cybersecurity manager might focus on three of them in the coming year. When they get management approval to pay for fixing all three of them, they’ve still got seventeen left for next year. The cybersecurity manager must make sure the owners of those remaining seventeen risks understand and accept this. The cybersecurity manager needs to say, “Hey, we have all these risks that we’ve decided not to do anything about this year. Let’s handle those in the coming years. Agreed?” After that moment, the cybersecurity manager is not responsible for those risks or their consequences should they materialise. We call this technique residual risk approval. Without residual risk approval, if the cybersecurity manager doesn’t notify anyone about a risk of ransomware that’s on the register but not in the top three, someone might later blame the cybersecurity manager for not telling anyone about it.
Management approval of residual risks lets you off the liability hook.
In essence, the cybersecurity manager must do three things: collect the right information, give it to the right people, and do it at the right time. Senior management expects the cybersecurity manager to keep track of all the risks, alert them of which ones are most important, and do it at a time when it can be budgeted for and acted upon. If you can do that, you will succeed as a cybersecurity manager.
Another challenge is that people tend to exaggerate the negative effects of risks, at least until it comes time to pay for fixing them. Then suddenly it doesn’t seem critical at all. So which is it? The cybersecurity manager has to sort through that confusion to get down to the few risks that actually are critical.
The cybersecurity manager’s first job is to find the critical systems—the crown jewels of the company. If these systems shut down, the business would shut down. They should be easy enough to identify, but as the cybersecurity manager asks people questions like, “How critical is your system to the business?” “What happens if it’s not available for a few hours? How about a day or two?” the responses may all sound alike. All the systems are considered critical by the departments that use them. But looking from the perspective of the whole enterprise, they might not be critical at all!
It’s up to the cybersecurity manager to assess the risks professionally and without emotion, and to help management prioritise them based on facts, not beliefs or opinions.
Choose the Right Methods
With hundreds of formulas for calculating risk out there, we have to be able to quantify and assess them, then implement the most appropriate one for our needs. As previously mentioned in this article, generally speaking, a risk formula takes the probability (P) and multiplies it by impacts (I), and that will equal risk. It’s not very complicated, but it’s only a starting point, and it is still how many companies do it.
There are hundreds of different formulas or more. The cybersecurity manager has to look up the few that are applicable to cybersecurity. He should understand how they work, why they are used, where they are used, and when not to use them. Then he can figure out which ones are applicable to which situations.
If you take a risk formula from an insurance company and use it in a manufacturing facility, it won’t work. It’s important that the right risk assessment methods and formulas are used for the right targets. For IT, use IT methods. For financial risk, use financial formulas for risk. If there’s a fire risk, you would use formulas applicable to fire risk management.
Ultimately, once you learn how to use risk management methods the right way, you can manage the downside of any opportunity and make it more likely to succeed and to turn out to be profitable.
Studies have done quantitative analyses of different companies with very large sample sizes. They found out that companies that do good risk management average a few percent more profit than the ones that don’t. A few percent greater profit is a huge deal.


