Cyber Threats For VIPs And Executives
Threats arising from cyberspace pose risks to both VIP individuals and the companies they associate with. Executive and VIP protection has traditionally been associated with physical security, but today, criminals target VIPs to gain access to high-value assets, to impersonate them in phishing campaigns (spear phishing attacks) or use their names and data in other fraudulent activities.
Therefore, protecting VIPs and executive’s personal information, credentials and other data belonging to them, should be an integral part of every organisation’s cyber defence strategy. By investigating VIP cyber exposure and proactively monitoring it on the dark web and deep web, an organisation can pick up early warnings and real-time threats that enable them to protect their business and their VIP stakeholders.
In today’s article, we will show you how effective VIP protection can be achieved with Cyber Intelligence House’s Cyber Exposure Platform (CEP).
Many Cyber-attacks would have been prevented if only the organisations had known how they looked from the outside"
A New Approach To Cyber Security
Traditional Cyber security services focus on helping organisations to address threats within their internal infrastructure and ICT Boundary.
However, the external world often presents the biggest threats and has the least visibility to the security team.
With Cyber Intelligence House’s Cyber Exposure Platform (CEP) you can evaluate the cyber exposure of any organisation’s executives and VIPs and instruct your client, prior to any attack, to act accordingly.
Ensuring VIP protection with CIH Cyber Exposure Platform (CEP)
Cyber Intelligence House’s Cyber Exposure Platform (CEP) is the leading technology for Dark web, Deepweb and Data Breach intelligence. Originally designed for law enforcement investigators, the service consists of the widest coverage of data from the dark web, deep web, malware logs and data breach records.
With the platform, you can offer VIP protection services to your clients by discovering:
- leaked credentials
- access for sale
- target lists
- attack preparations
- reconnaissance operations
- discussions
- or other malicious activity
Let’s take a look at how this is done through specific examples.
Using the CEP - Investigation module: How to conduct an investigation?
The investigation module is part of the Cyber Exposure Platform (CEP) and a tool to search for data on specific targets. Initially designed for law enforcement, this powerful feature is now available on the CEP for our MSSP (Managed Security Service Provider) clients. You can investigate the cyber exposure of your VIP client in a matter of seconds with the easy-to-use search functionality and store the findings for precise reporting.
On the investigation module, you can define a data type for each search term. CIH’s automated data import pipeline parses many types of items from pages, and these items are stored on lists for more rapid searching capability.
Supported data types are:
- Text
- Numbers
- URLs
- addresses
- bitcoin
- credit cards
You can do searches by using the Executive or VIP’s name. As an example, I will use my name.
In a matter of seconds, search results are returned, exposing all the findings that include the VIP name from CIH’s massive database of Darkweb, Deep web and data breach data.
This database has been built up over ten years and is the world's most comprehensive dataset of its kind.
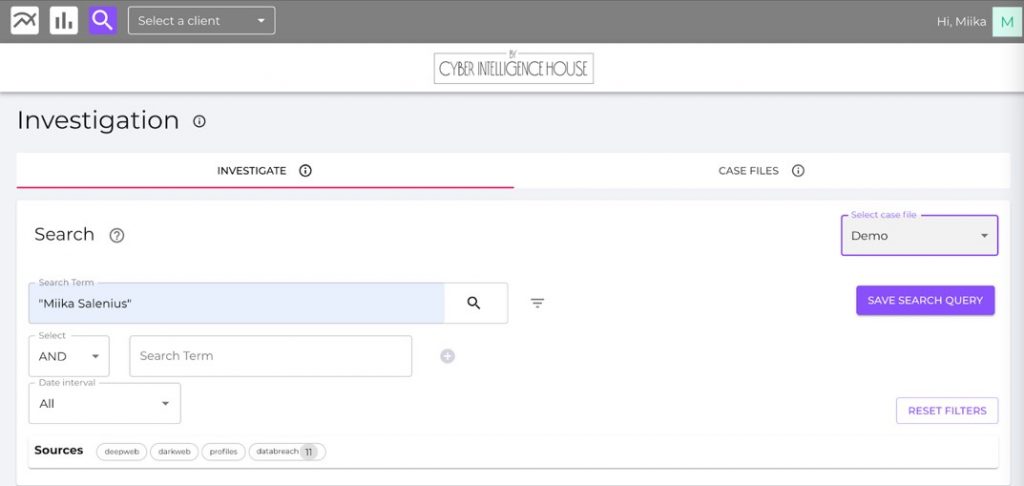
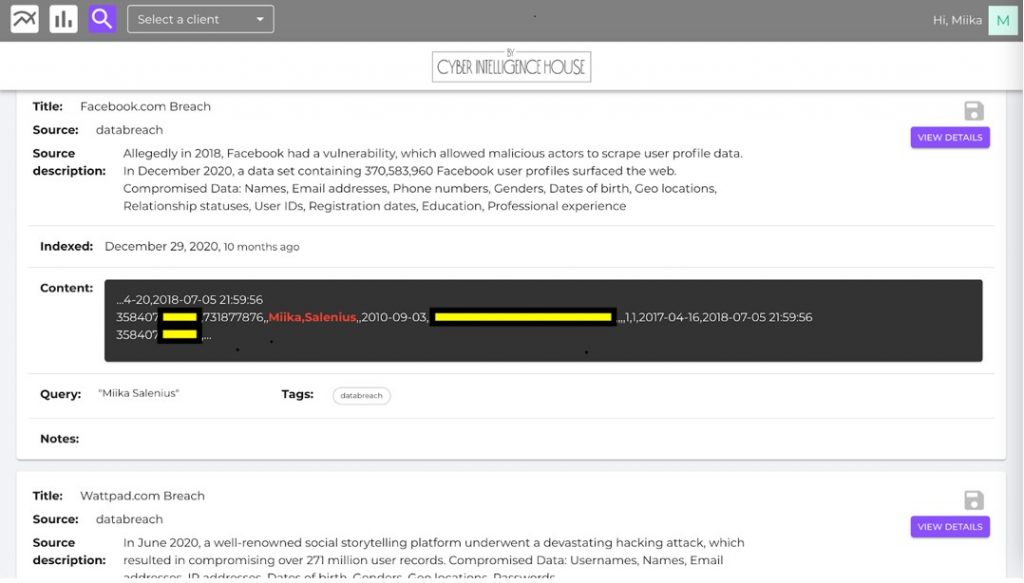
The results reveal 11 findings from data breaches. Let’s take a closer look at some of the findings.
Subscribe To Our Newsletter
Get the latest intelligence and trends in the cyber security industry.
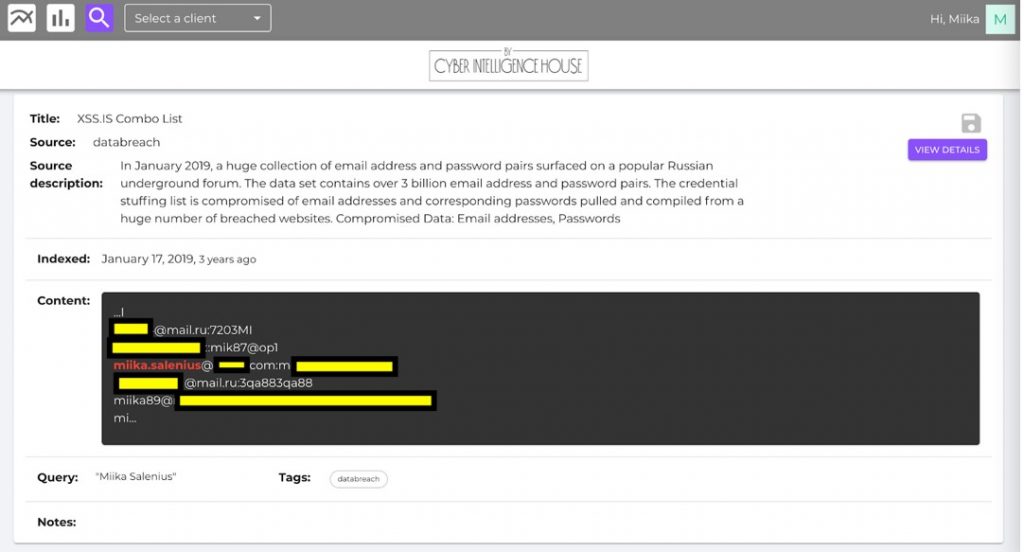
Looking at the two example findings, we immediately notice information directly related to the VIP name. We have telephone numbers, email addresses, passwords, home locations, usernames. We have telephone numbers, email addresses, passwords, home locations, usernames. We can save all relevant findings into a case file which allows us to easily get back to individual findings at any time.
Now that we have the relevant information at hand, we can use the additional data to create other search keywords. This allows us to conduct a deeper investigation and get a complete picture of the VIP’s cyber exposure. It is very much like a real-world investigation, where you follow each clue you encounter and combine it into an investigation thread until there are no more findings or leads to take you further.
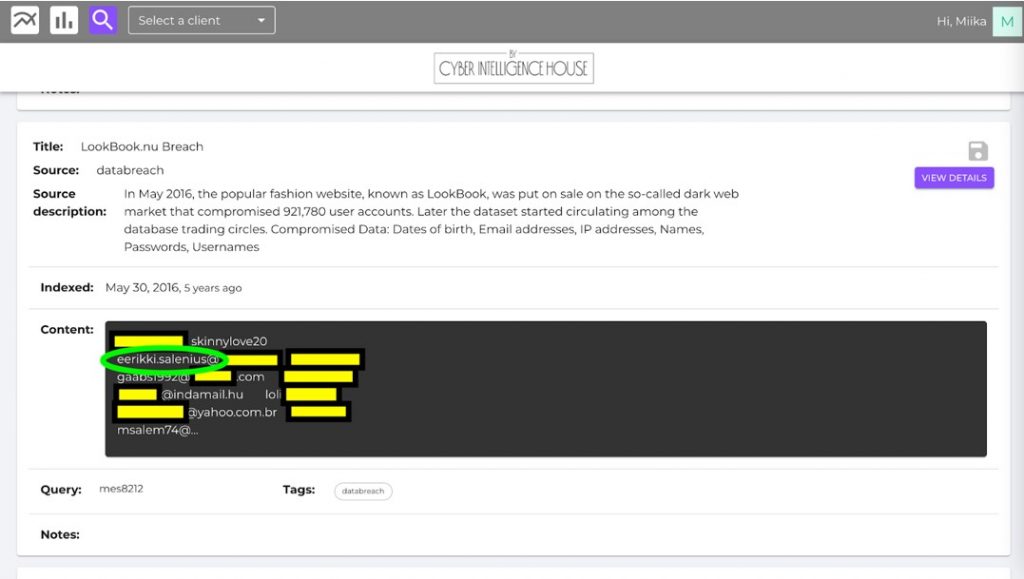
Another great feature the investigation module provides is allowing you to place boolean operators such as “and, or, not” into your search. E.g., you could search for malware logs related to the VIP.
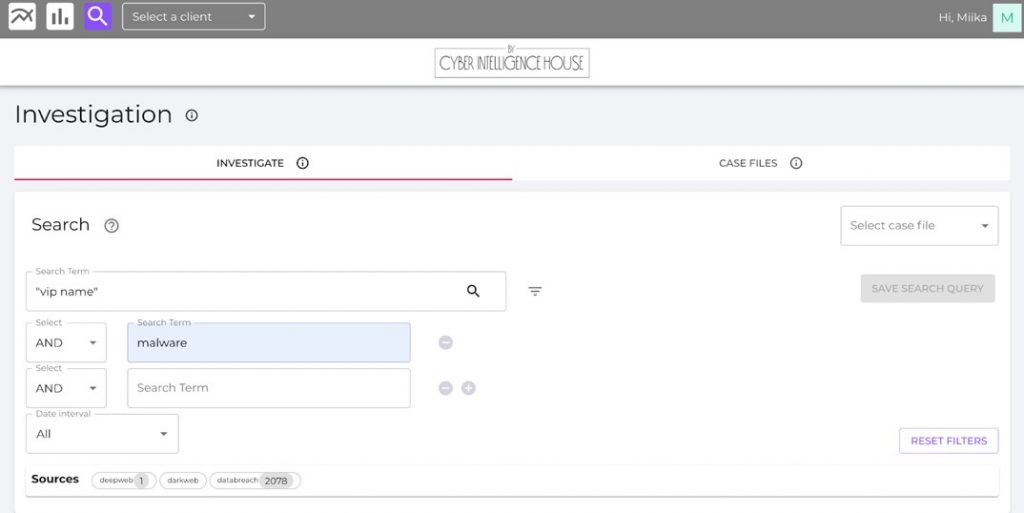
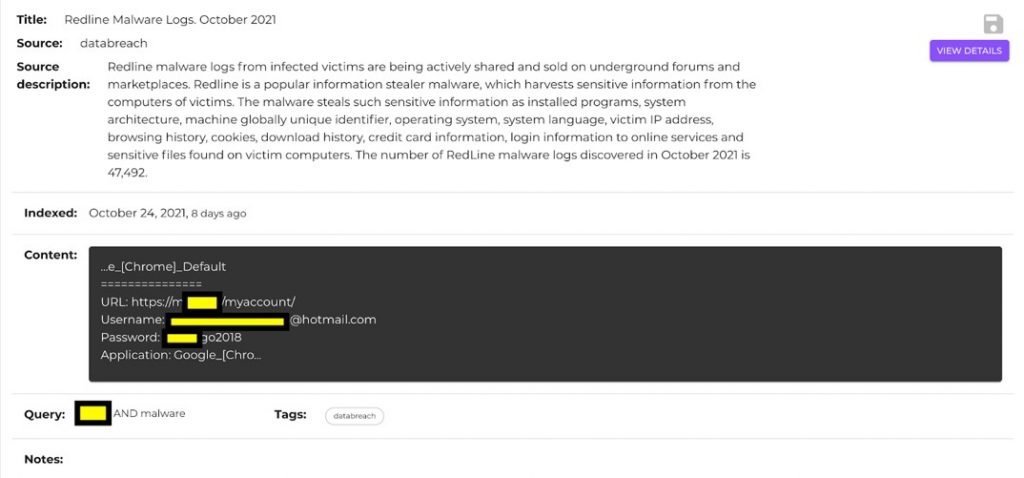
If there are malware findings related to the VIP, it would mean a jackpot for an attacker. They are one of the hottest items on the dark web and deep web marketplaces, and they, unfortunately, reveal all the usernames and passwords that a VIP or Executive has been using with an infected computer (for professional or personal matters).
There are a growing number of malware logs in the CIH database, which will create alerts if the username matches your VIP’s keywords. So there is a high probability that if your customer’s credentials are compromised, they can be found on our platform.
Using the CEP Assessment module: How to identify VIP and executive organisation's assessment?
The second way to conduct VIP protection with the Cyber Exposure Platform (CEP) is to use the Assessments module, which is designed to assess any organisation’s past and present state of cyber exposure – the harmful visibility in cyberspace that can impact any organisation’s performance and business objectives.
The assessments are generated through the analysis of externally observable data collected from the dark web, deep web, malware logs and data breaches.
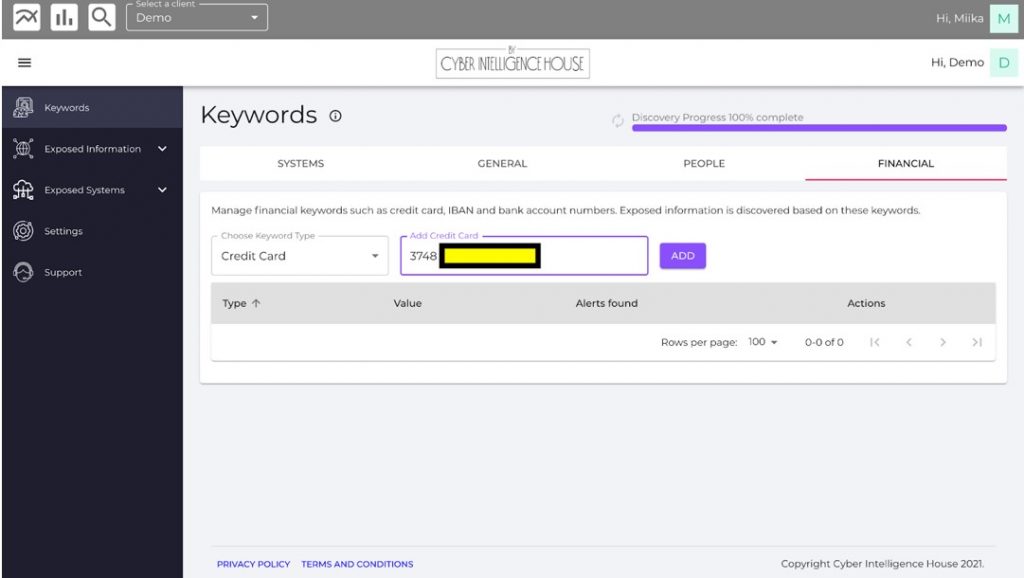
The assessments are conducted based on relevant keywords. In the case of executives and VIPs, we can use names, email addresses, telephone numbers, usernames, credit cards or other relevant information. There are no limitations on the number of keywords you can use in the assessment module. However, all keywords should be as unique and relevant as possible to avoid unnecessary “noise”.
As you can see in the picture below, you can also search for financial information like credit cards, bank accounts, or IBANs.
Once the keywords are in, the results are searched directly from our database. Results will be provided in a matter of seconds. Our database is continually growing at an increasing pace with information from the dark web, deep web, hacker forums, Marketplaces, new data breaches and malware logs.
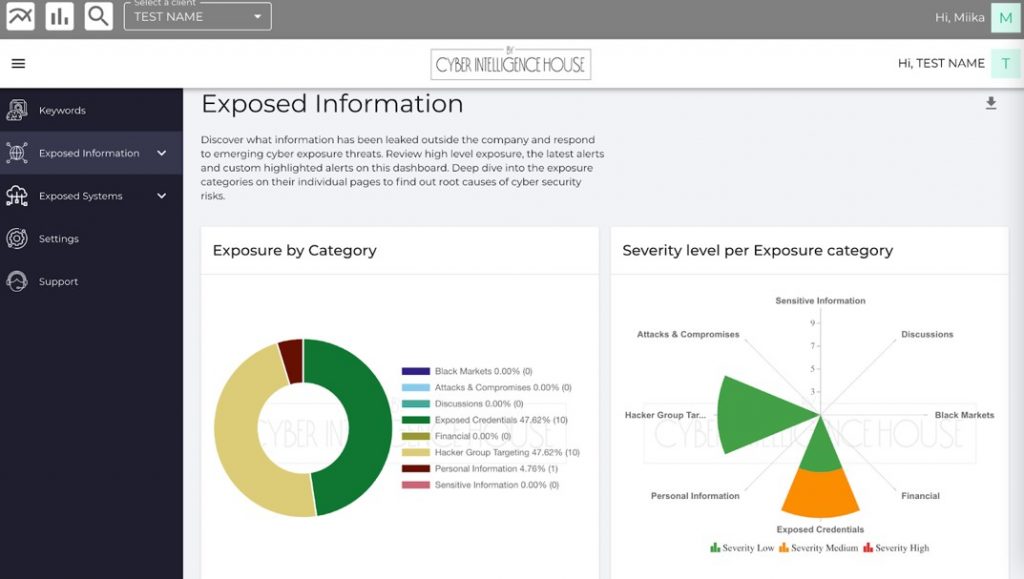
The Assessment module comes with highly sophisticated Machine Learning (ML) and Natural Language Processing (MLP) algorithms. These advanced techniques interpret each finding based on the source and context of the result. It uses over 250 metadata factors to contextualise and categorise the findings into different cyber exposure domains. The automation is unique to CEP and provides powerful insights, easy data analysis and effective actionability.
Continuous automated monitoring
The two examples above are both ways to get a picture of the overall cyber exposure at a certain point in time. It shows present and historical information, but what if you want to create recurring revenue by offering your customers continuous services?
CEP allows you to set up 24/7 monitoring for your clients easily. Continuous automated monitoring helps organisations discover exposed information about themselves, including their executives and VIPs, and enables them to respond to emerging cyber exposure threats whenever they appear in the dark web, deep web or data breaches.
CIH’s data acquisition team covers over 20 languages and manually acquires access to restricted marketplaces, leak sites and discussion forums. The exposed information is collected automatically by proprietary collecting robots and enriched with metadata factors for searchability and contextualisation.
VIP protection through a continuous feed can be achieved with both the investigation and the assessment module. To learn more about the Cyber Exposure Platform and test it for yourself, contact our team today.


