What Is The Dark Web?
The dark web refers to the internet’s encrypted areas known for providing anonymity to the hacker. The dark web is a subset of the deepweb. It is intentionally hidden, requiring a specific browser—Tor.
This part of the internet isn’t visible to search engines and requires the use of an anonymizing browser like Tor to be accessed.
It is an illegal marketplace to sell out an organization’s crucial information, publicize the private documents of any organization, or use the essential data to send invoices to the customers for fraud.
The dark web is simply the internet content on darknets, which don’t allow indexation to search engine crawlers and can only be accessed by specific software, configurations, or authorization. It overlays networks that may be peer-to-peer networks or large public networks such as Tor (dark web browser), Riffle, or Freenet.
How Much Of The Internet Is The Dark Web
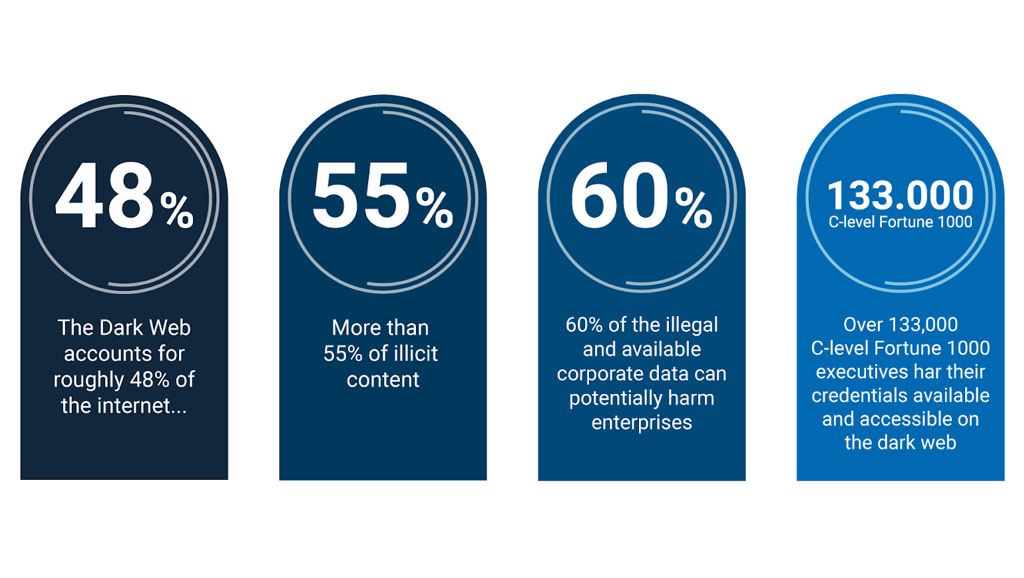
The dark web accounts for roughly 5% of the total internet
Why Does It Represent A Threat To Business?
How Are Businesses Affected By Dark Web Malpractices?
Small and Medium Enterprises (SMEs) are prey to the criminally minded people who try to exploit the organization’s systems to gain financial data, customer credentials, employee social security numbers, and account logins. The main objective is to sell and make a profit with stolen data.
Many executives don't have much idea about dark web threats. It brings a significant disadvantage when it comes to protecting business and customer data
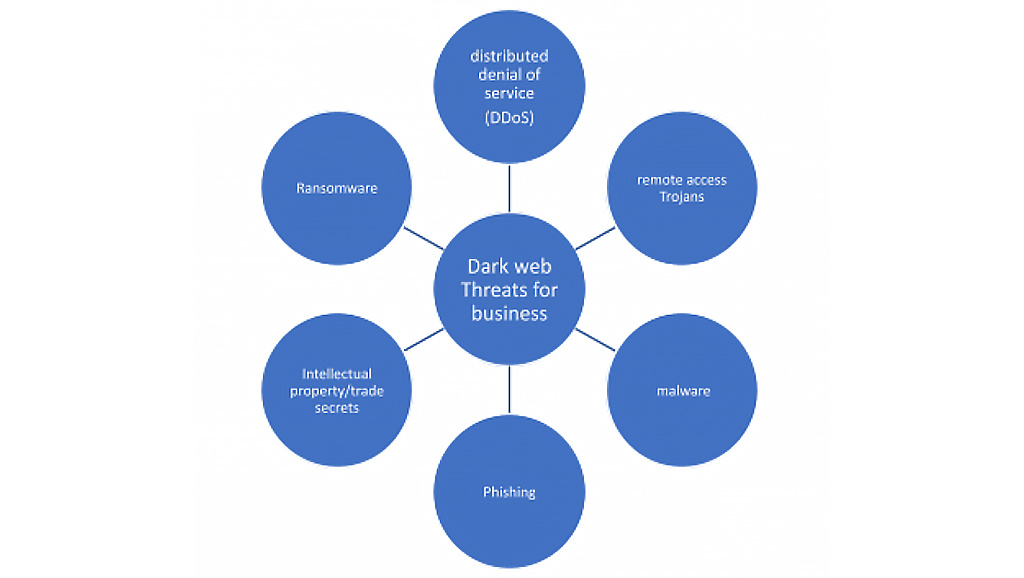
The anonymity that the dark web provides to a person allows him to try and break the security firewalls and get access to the company’s network system. The prevalent method of breaching into the sensitive areas of your employee’s computer is Phishing. The hackers try to impersonate the email forms and the login pages of legitimate websites or even your prospective clients. Once you login to these pages, the sensitive login information already gets stored with the hackers. They can easily use the login information to reach sensitive documents that you would never want to publicize.
Nowadays cyber attacks are also used for Industrial espionage (h3)
Breaches occur and would continually happen, despite the very best attempts of cyber security professionals working worldwide. Cyber-criminals are very well aware of the human tendency to keep the same password in all of their accounts, sometimes even the business account. Thus, if the hacker manages to get your Facebook or Instagram password, they may likely break into your business account details as well. Cyber miscreants can only be successful if you fail on your side. Try to keep stronger passwords, use two-factor authentication, and frequently change the password. The small steps may need effort and will, but they can protect you from significant complications.
However, a policy to have strong passwords and two-factor authentication is not enough in today's world. Every organization needs to be proactive and ahead in terms of cyber security
Subscribe To Our Newsletter
Get the latest intelligence and trends in the cyber security industry.
What Information Are The Cyber-Miscreants Looking For?
When hackers are trying to breach your company’s private information, they may most likely attack the business’s credit card numbers, the payment information saved by your customers, and your financial reports. The credit card data can bring monetary gains to them. Also, third parties are looking to buy your financial statements or the email list to check on your progress. The leak of the customer’s details can bring you shame and disrupt your reputation in the market. These breaches also lead to lawsuits, meanwhile damaging the business abruptly.
Loss Of Customer Loyalty Due To Customer's Data Breach
The customer’s trust is the most important thing for any company or business. The studies show that the majority of the transactions of an SME are from loyal customers. It is way easier to sell to an existing customer than acquiring a new customer. The loyal customer base is the backbone of any business. The worst thing that could transpire to a business is losing the trust of their loyal customer base. Data breaches do precisely the same.
If a consumer trusts a company and saves their payment credentials for further transactions, they expect the company to install sufficient firewalls and take steps to preserve their data. Thus, it is the organization’s responsibility to keep up the trust. If they fail in it and data breaches happen, they lose the ever-aspired customer trust and bond. The business can improve their protection later, but they are not expected to perform as previous. Everybody has concerns regarding their privacy. Thus, the company can restore the data later, but it isn’t easy to rebuild the hampered reputation.
UNODC Report
According to a report of UNODC, the use of darknets has increased in the last few years. The COVID-19 pandemic seems to have significantly intensified the trend. The young urchins with no previous cybercrime record seem to indulge in data breaching and other cybercrimes. New people have also begun seeking aid from experienced darknet criminals concerning illegal chances. Darknet illegal marketplaces have become common during the COVID-19 pandemic, owing to some combination of technology offering higher anonymity for the buyers and sellers. Features like accessible payment approaches and standing metrics have increased.
Cryptocurrencies are the first choice for illicit transactions, but the use of crypto-mixers, tumblers, or laundry services violates the link purchase and the final purchase destination. Such loopholes in the system make it very difficult to bring the risk-offenders to justice.
How To Know If A Company's Corporate Data Is On The Dark Web?
Probably the first thought is how to get on the dark web? However, in order to scan and analyze all the available information you will need tools that scrape tons of terabytes of data.
Why Is Dark Web Scanning And Dark Web Monitoring So Important?
Dark web scanning is the non-stop process of searching and monitoring the data on the dark web. The dark web scanner continuously tracks the private networks, blogs, and other sensitive areas of the dark web to see whether the business’s information has been mentioned anywhere. You can instantly seek an IT professional’s help to limit the damages caused due to the data breaches. Every single method is worth it to prevent the dark web data breach. It damages the reputation and shakes customer loyalty and creates a massive loss in revenue.
How To Protect Any Business Or Organization From Cyber Attacks?
Understanding the consequences of data breaches and other potential threats that the dark web poses to business is the most crucial step towards data protection. The world has experienced a digital revolution. Hence, every successful business is online to increase its brand presence and sales. The biggest hurdle is to keep oneself and the business safe in the world of piracy, cyber interventions, and data breach.
The online presence is very vital for your growth. From accessing any B2B service to having an online purchase, the traditional method has faded away. The world is digital, and digitalization is here to stay. There are potential threats, and you need to overcome them to achieve milestones. The priority should be to keep oneself safe from cyber-criminals and protect the crucial data and information vital to your business.
Cyber Intelligence Platform is designed to help Managed Security Service Provider (MSSP) increase and improve their workflow and pipeline of clients.
To know how CIH proprietary Cyber intelligence platform can help you scale your business please apply for a test-drive.


